Which of the Following Authentication Methods Is 100 Percent Accurate
ASmart cardBFingerprint authentication CUser ID DNone of the above None of the above authentication methods are 100 percent accurate. Which of the following authentication methods is 100 percent accurate.
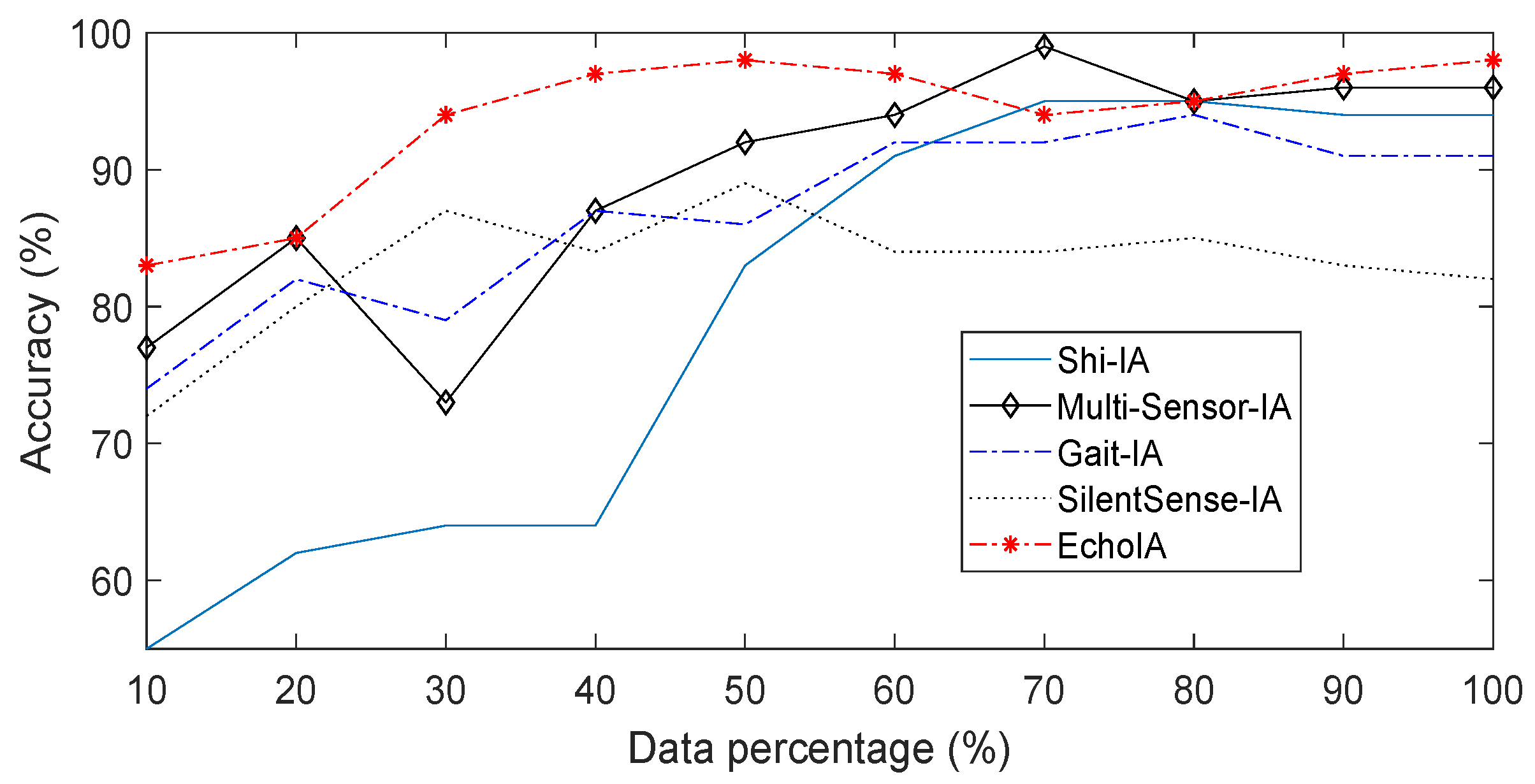
Network Free Full Text Echoia A Cloud Based Implicit Authentication Leveraging User Feedback Html
The use of biometrics has many benefits.
. What is social engineering. False Which of these biometric authentication methods is not as accurate as the rest. Even slight variations in how a user touches a fingerprint scanner or looks at a camera during a facial scan will create different images.
What you must understand is the difference between the various options and what their advantages and disadvantages are. Which of the following authentication methods is 100 percent accurate. By contrast scanners used to capture and read biometric data arent accurate 100 percent of the time.
Voice pattern What is meant by physically constrained user interface. 160Where do organizations typically place firewalls. The Second Line of Defense Technology 246p.
None of these are correct. In addition to examining well-known multimodal methods we introduce novel methods of fusion and normalization that improve accuracy still further through population analysis. A method for confirming users identities.
Through what you are your fingerprint your hand your face. There is no other type of authentication that is so readily visible and. In contrast to passwords badges or documents biometric data cannot be forgotten exchanged stolen or.
Which of the following authentication methods is 100 percent accurate. None of the above. User Datagram Protocol UDP Role-based access control RBAC means limiting users access to database views as opposed to allowing users to access data in database tables directly.
Highly accurate COTS systems on a relatively large-scale population. User id bsmart card cfinger authentiation. None of these Fingerprint authentication User ID Smart card.
None of the above. Fingerprints have been used as a form of identification for well over 100 years. Your biometrics are often all over the place eg fingerprints or face or can be captured by anyone following you around.
The resulting discrepancies can cause authentication to fail and lock legitimate users out of the system. Which of the following authentication methods is 100 percent accurate. Terms in this set 15 What is the most costly and intrusive form of authentication.
The leading one is the level of security and accuracy that it guarantees. Which of the following authentication methods is 100 percent accurate. Which of the following authentication methods is 100 percent accurate.
Which of the following is not one of the three primary information security areas. 1 Easy Learning Outcome. Utilizing something you know a name a secret or a password.
A user interface that does not provide. None of these are authentication methods are 100 percent accurate. It is never possible to have all of the information required to make a 100 percent accurate prediction.
No one form of biometric authentication is going to stand head and shoulders above the rest. Which of the following authentication methods is 100 percent accurate. Which of the following authentication methods is 100 percent accurate-Fingerprint authentication-Smart card -User ID -None of the above.
A fingerprint authentican b. Something that is part of the user such as a fingerprint or voice signature. Introduction It has recently been reported 1 to the US.
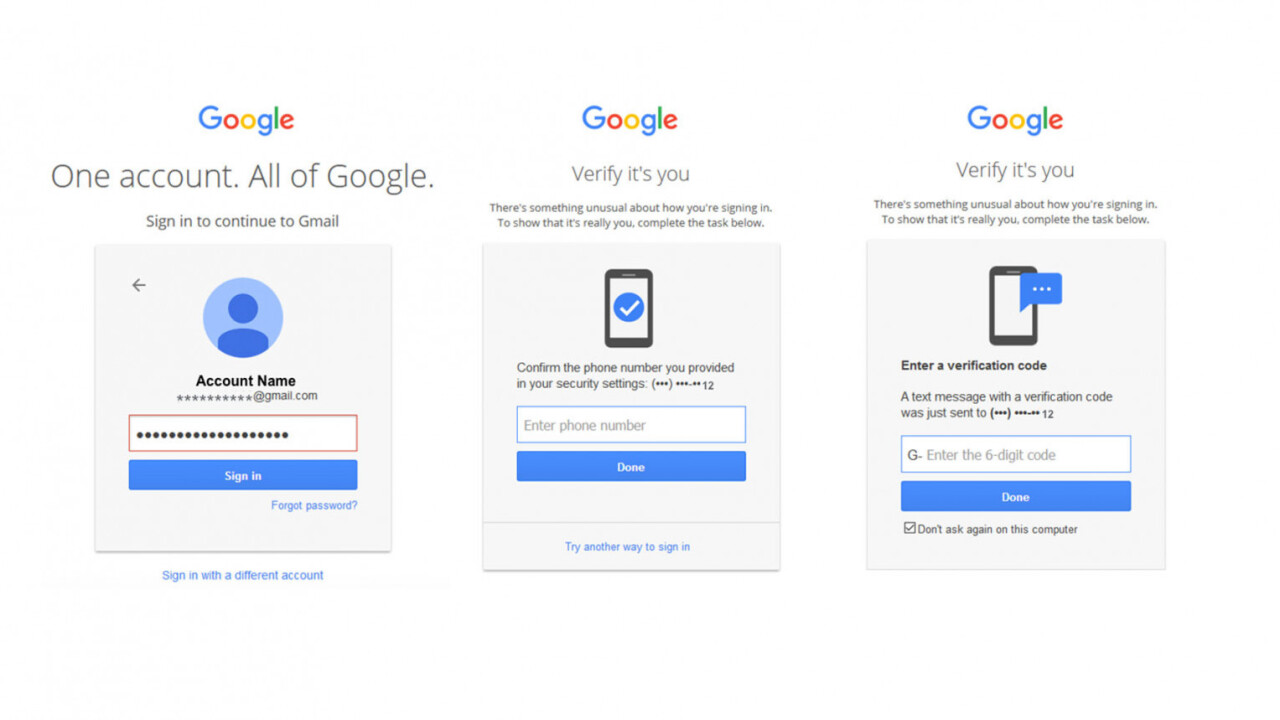
Google Data Shows 2 Factor Authentication Blocks 100 Of Automated Bot Hacks
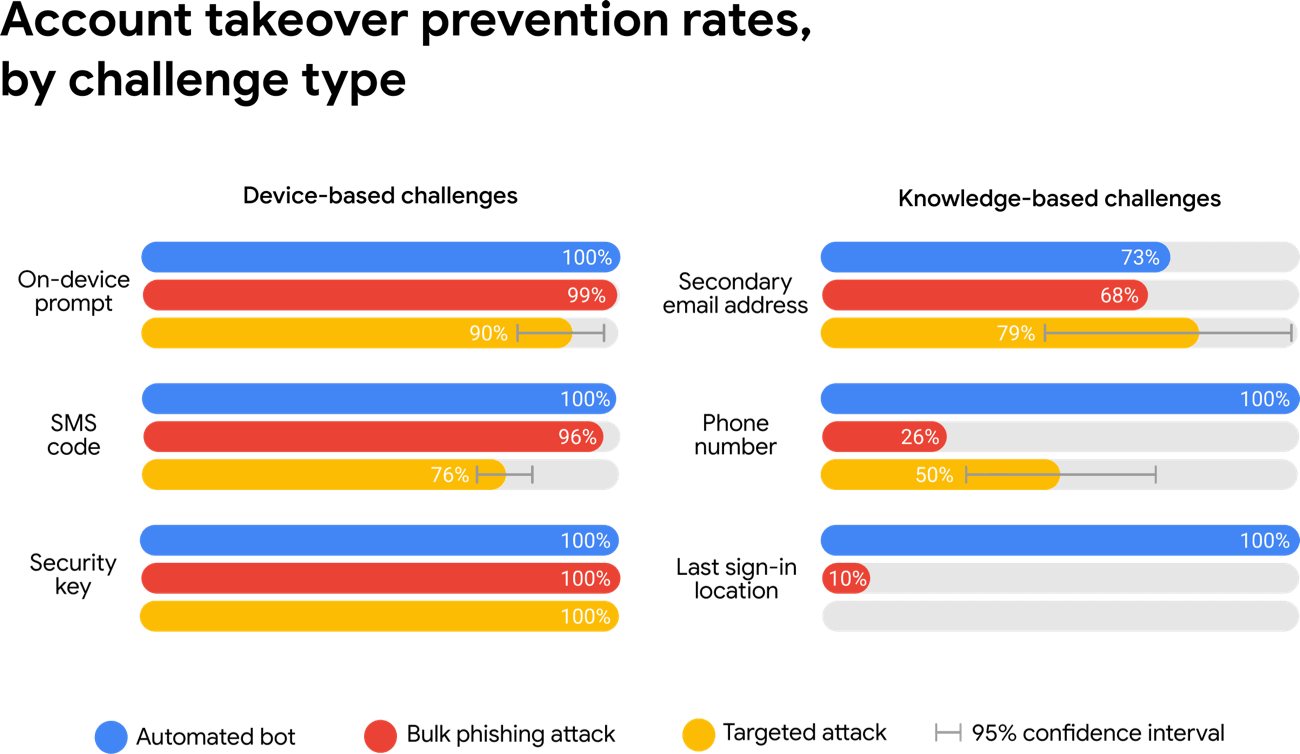
Google Data Shows 2 Factor Authentication Blocks 100 Of Automated Bot Hacks
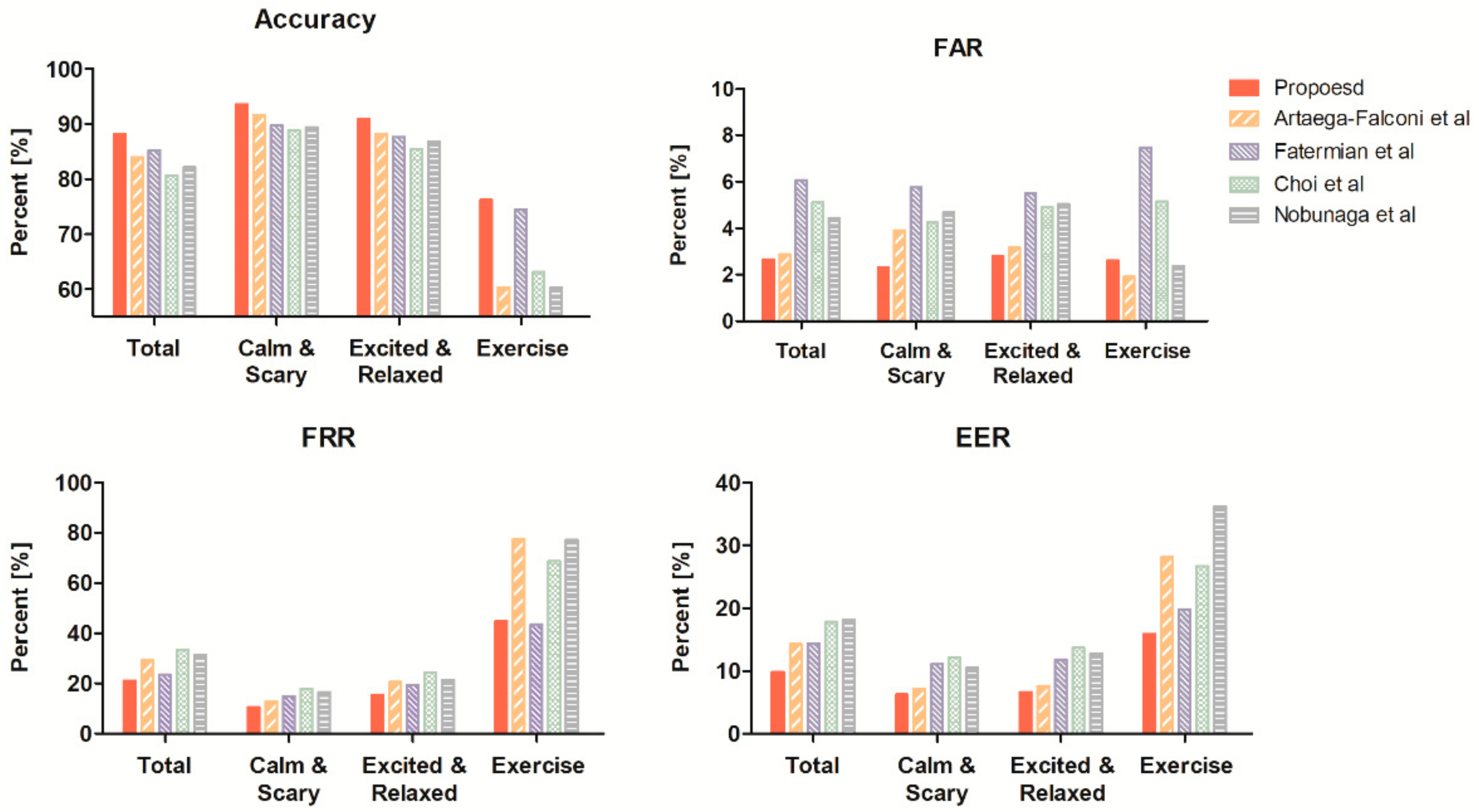
Sensors Free Full Text Ecg Authentication Based On Non Linear Normalization Under Various Physiological Conditions Html
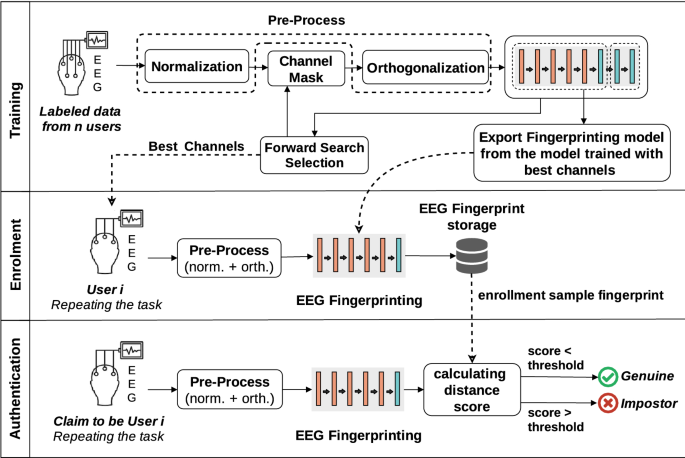
Towards A Universal And Privacy Preserving Eeg Based Authentication System Scientific Reports

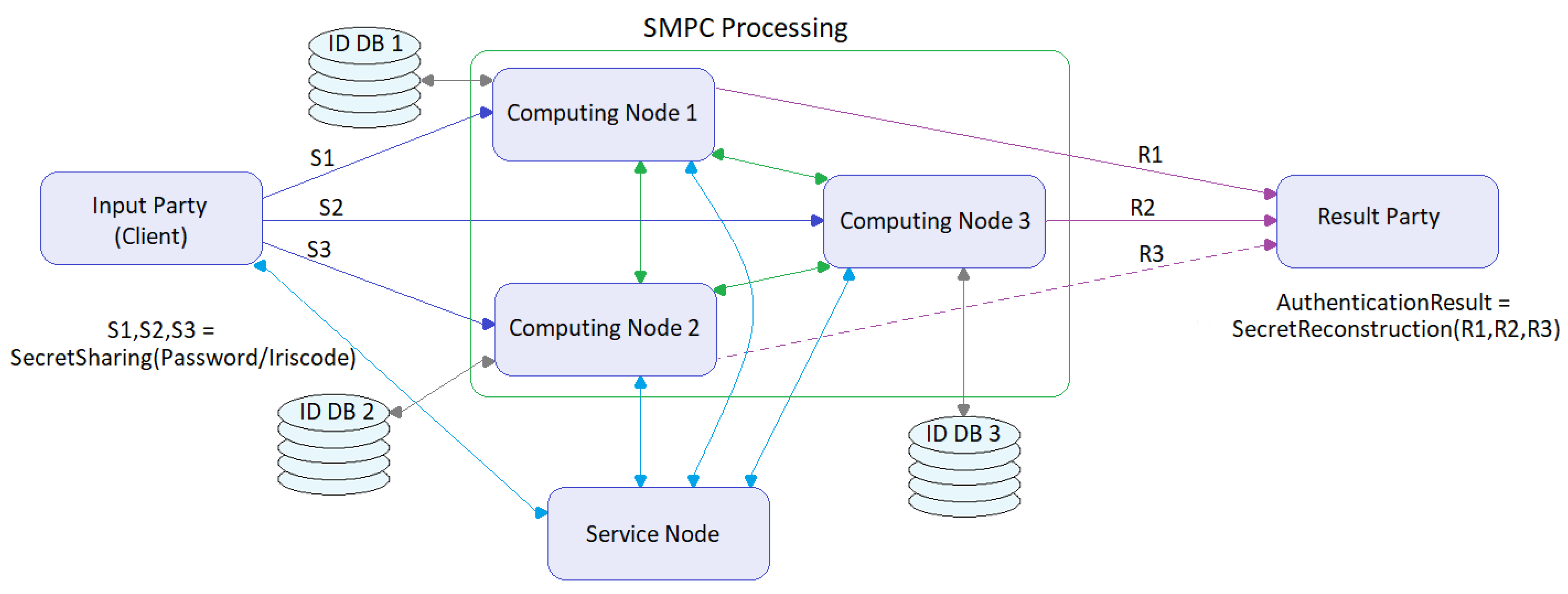
Symmetry Free Full Text Assessment Of Two Privacy Preserving Authentication Methods Using Secure Multiparty Computation Based On Secret Sharing Html
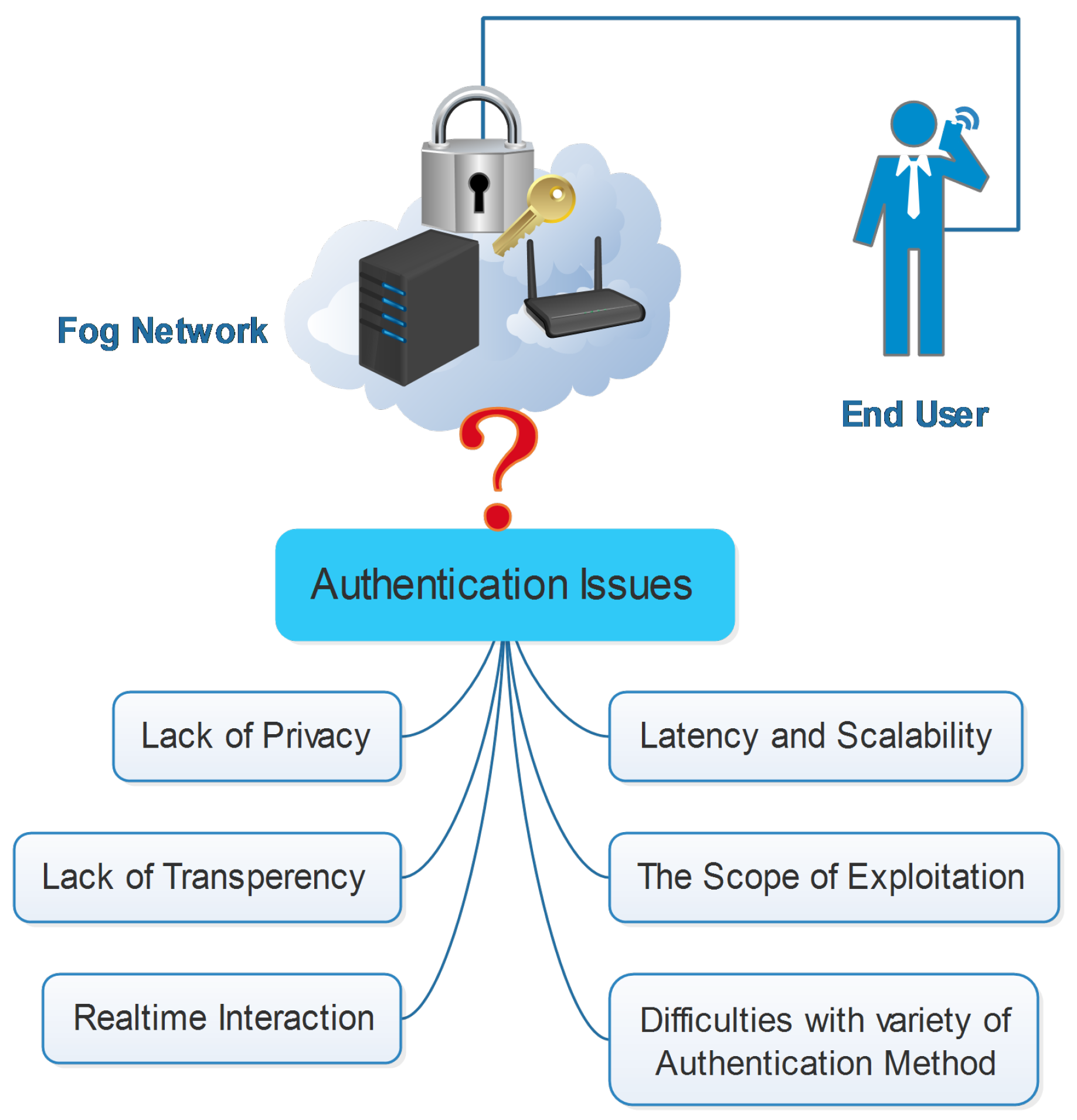
Electronics Free Full Text Towards Secure Fog Computing A Survey On Trust Management Privacy Authentication Threats And Access Control Html
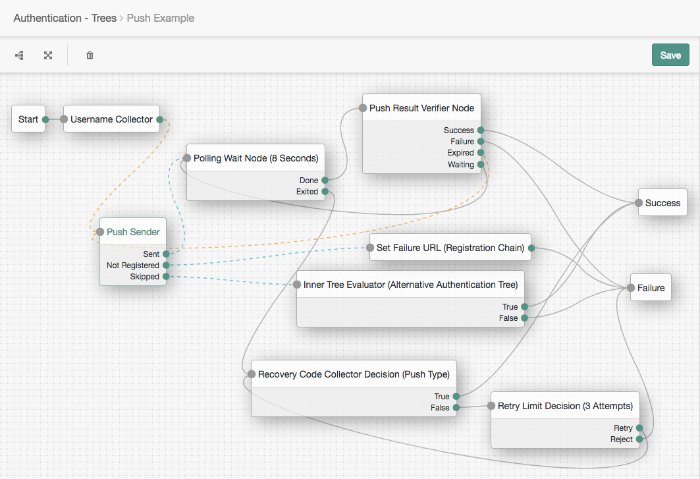
Forgerock Access Management 6 5 Authentication And Single Sign On Guide

Sensors Free Full Text Ecg Authentication Based On Non Linear Normalization Under Various Physiological Conditions Html

Mis Chapter 4 Quizzes Flashcards Quizlet

Pdf Security And Accuracy Of Fingerprint Based Biometrics A Review
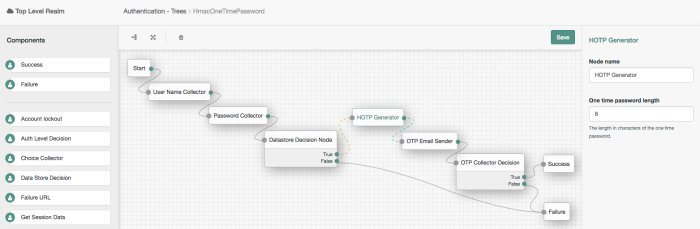
Forgerock Access Management 6 5 Authentication And Single Sign On Guide

5 Authentication Methods Putting Passwords To Shame

Pdf Sip Security Issues The Sip Authentication Procedure And Its Processing Load

A Systematic Literature Review Of Empirical Methods And Risk Representation In Usable Privacy And Security Research Acm Transactions On Computer Human Interaction
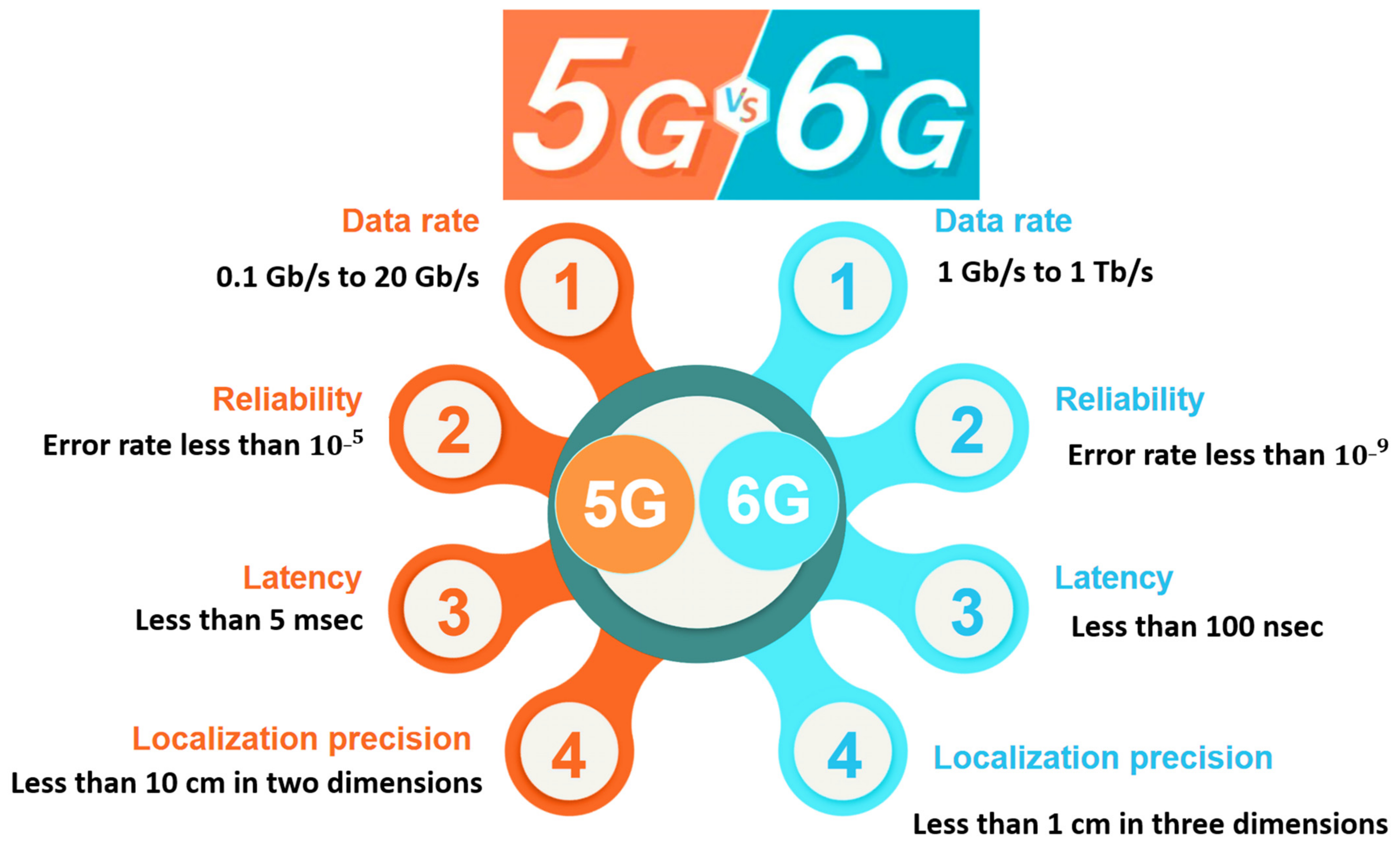
Sensors Free Full Text Security Requirements And Challenges Of 6g Technologies And Applications Html
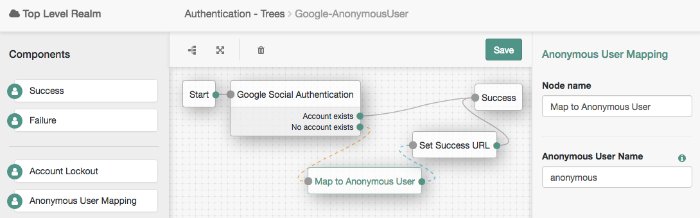
Forgerock Access Management 6 5 Authentication And Single Sign On Guide

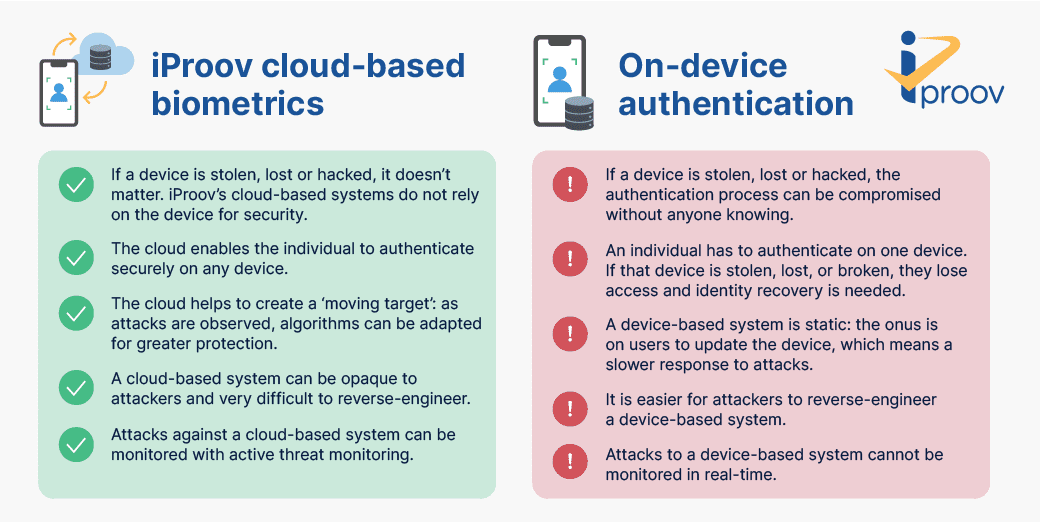
Comments
Post a Comment